Security infosheet
This document was last updated on October 8, 2025
Intro
The purpose of this document is to summarize the technical architecture of Anchorpoint, including the security and privacy measures implemented by Anchorpoint to protect customer data.
About Anchorpoint
Anchorpoint is a Version Control and Digital Asset Management (DAM) solution. Its purpose is to facilitate the organization of files and tasks within projects that involve the creation of digital content such as video, real-time 3D graphics, animation, or still images.
Creating this type of content requires complex file exchanges and file structures, which Anchorpoint helps to organize. It provides a set of tools that includes version control, tagging, search, and comments & annotations directly on a file, without uploading it to a cloud server.
Anchorpoint is a desktop application, designed to work like a file browser that manages metadata (tags, annotations, comments, and so on). Users provide their own solution for file storage, and Anchorpoint reads the files on that storage and adds the metadata.
How does Anchorpoint manage files?
Anchorpoint does not modify production data, which is defined as project files, code, videos, images, 3D models, Blender or Photoshop files, etc. This data is stored in a Git repository or a shared folder on a user's hard drive, Dropbox, Google Drive or NAS. Anchorpoint adds metadata, such as file locks, tags and annotations.
Where is Anchorpoint's metadata stored?
Anchorpoint processes metadata (tags, file locks, attributes or shared Git config values) in the Anchorpoint cloud, facilitating team collaboration or synchronization across multiple computers.Anchorpoint stores a .approj file in your project, indicating the location of your project files (described above). Anchorpoint does not upload any production data to the Anchorpoint cloud.
Components & sub-processors
Anchorpoint’s cloud hosted vs self-hosted solution
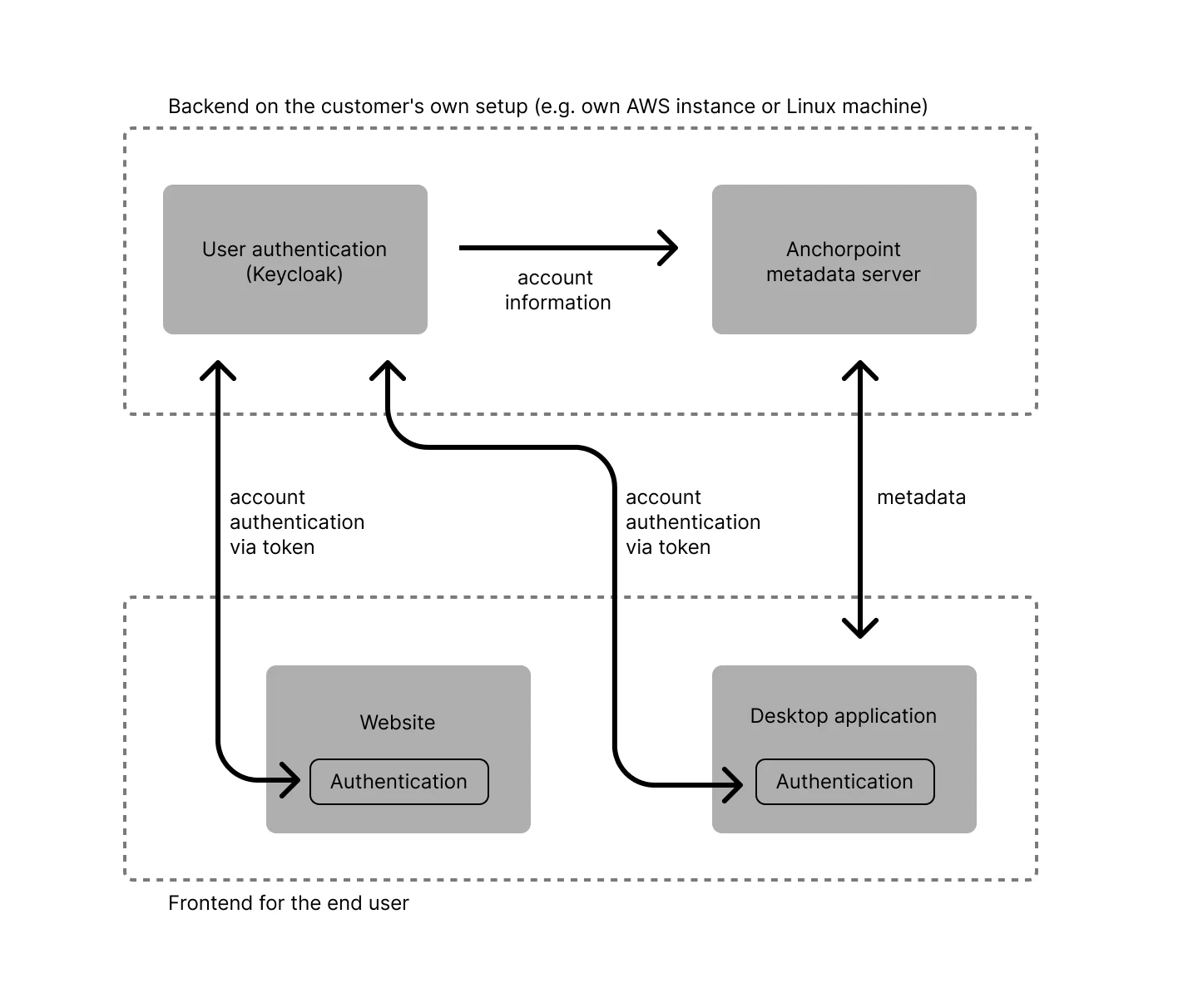
The following paragraphs describe Anchorpoint’s “Cloud Metadata” solution which is using a backend server for managing metadata that is hosted within our environment. As part of the Organization Plan, users can also choose to self-host that server within their own environment. The self-hosted metadata server, does not connect to any of our cloud services and therefore does not use any external sub-processors. Read more about the setup instruction on the self-hosted metadata server.
Application architecture


Account information
Account information helps Anchorpoint to connect data to an existing account, and provides the necessary information for granting permission to data and features. It does not include payment information. Account information consists of:
- Email / Social login information (e.g. Name or Profile Image)
- Subscription tier
- Number of purchased seats
Website
The Anchorpoint.app website allows access to the user login and is required within the login flow of the desktop application. It redirects to the user authentication (Auth0 with OAuth2) and receives a token that indicates the login status on the website. In case of payment, it redirects to Stripe payment processing.
Metadata
This is the data required to perform fundamental tasks in Anchorpoint. Metadata can be represented as projects, tags, annotations, comments, versions, or reviews; all of which are string-based data stored in a relational database.
Anchorpoint also stores binary data in the form of PNG image files, such as user-replaced file thumbnails, project icons, and customized user icons. This binary data is stored in an AWS S3 bucket.
Anchorpoint server
The Anchorpoint server is operated by the Infrastructure as a Service (IaaS) provider Amazon Web Services (AWS). The corresponding datacenters are located in Frankfurt, Germany, with instances running on eu-central-1a, eu-central-1b, and eu-central-1c.
This entity stores the metadata using an Amazon Aurora PostgreSQL database. This data is then sent to the entitled Anchorpoint desktop application. It does not store critical user data, such as passwords and credit card information.
Desktop application
This is the main interface that represents the metadata to the end user. It also provides the tools to create, edit, and remove metadata. The data is also stored in an offline cache to improve performance and is synced with the Anchorpoint Server. Therefore, only user-accessible metadata is synced to the offline cache. To be able to access or modify data on the Anchorpoint server, OAuth2 authorization code flow is used. An obtained refresh token is stored AES 256-bit encrypted in a local cache and has a maximum lifetime of 30 days. Refresh Token Rotation is enabled, which prevents the reuse of an already used refresh token. The according AES encryption key is saved in the platform-specific credential manager (macOS Keychain and Windows Credential Manager). Obtained access tokens are only held in memory and have a maximum lifetime of 1 day.
The Desktop Application does not have access to the user login credentials (OAuth2 flow via Auth0) or read or process any kind of payment information (only accessible in Stripe).
User authentication (Auth0)
For managing user accounts, Anchorpoint uses the Auth0 platform by Okta Inc. Auth0 is an external provider for user authentication solutions which is certified by ISO27001, ISO27018 norms and is also SOC 2 Type II and GDPR compliant.
The user can create an account via Auth0 and can log in via authorization code flow on Auth0 and get redirected to the desktop application. The desktop application resolves tokens via the resulting code and saves them as described in the previous section.
User authentication for the self-hosted metadata server (Keycloak)
Using the self-hosted metadata server, Keycloak is used instead of Auth0 as the user authentication component.
Payment processing (Stripe)
Payment and payment information is stored and processed via Stripe Inc. It complies to the PCI DSS norm and is certified as a PCI Level 1 service provider. No payment information is stored or transferred out of Stripe to the Anchorpoint Server. Stripe provides the following account information to the Anchorpoint server:
- Number of seats
- Tier Plan Information
Technology providers
AWS
Anchorpoint's server runs on AWS (Amazon Web Services). AWS is the market leader for Infrastructure as a Service (IaaS) and provides all the necessary security and compliance requirements for our products.
Anchorpoint uses EU data center regions. Data is hosted in Frankfurt am Main, Germany, with instances running on eu-central-1a, eu-central-1b and eu-central-1c.
AWS is fully ISO 27001 certified. Further information and the certificate can be found here: https://aws.amazon.com/de/compliance/iso-27001-faqs/.
Additional certifications
- CSA/CCM report: https://aws.amazon.com/compliance/csa/
- TISAX report: https://aws.amazon.com/de/compliance/TISAX/
- GSHB report: https://aws.amazon.com/de/compliance/bsi-c5/
- PCI/DSS report: https://aws.amazon.com/de/compliance/pci-dss-level-1-faqs/
- SOC2/Type2 report: https://aws.amazon.com/de/compliance/soc-faqs/
- ISO 27017/18 report: https://aws.amazon.com/de/compliance/iso-27017-faqs/
Auth0
Auth0 is the authentication system that manages user accounts and generates tokens, allowing a secure connection between the desktop application and the server. This procedure follows the OAuth 2.0 protocol.
Auth0 is also fully ISO 27001 and ISO 27018 certified and complies with the following policies and certifications.
- SOC 2 Type II: https://auth0.com/blog/auth0-achieves-soc-2-certification/
- HIPAA BAA: https://auth0.com/learn/why-hipaa-compliance-is-vital-your-business
- Gold CSA STAR: https://cloudsecurityalliance.org/star/registry/auth0/
- PCI DSS Compliance
- GDPR: https://auth0.com/docs/secure/data-privacy-and-compliance/gdpr
Stripe
Stripe is used to process payments and store payment information. It has been audited by a PCI-certified auditor and is certified as a PCI Service Provider Level 1, the highest level of certification possible in online payments. For more information about security at Stripe, please visit this link.
Connections between services
Backend hosted on AWS
Database
Runs on a private subnet of a VPC (only internal communication possible).
Application
Runs on a private subnet of a VPC (only internal communication possible). Communication to other backend components like database, message broker, or load balancer happens over non-TLS connections. No external outbound connections to external services (like Stripe or Auth0) are used.
Load balancer
Performs TLS termination of external requests on outbound-facing port 443 mapped to internal port 80
Message broker
Runs on a private subnet of a VPC (only internal communication possible).
External services
Stripe
Uses a webhook over TLS connection terminated by AWS load balancer and passed to the application.
Auth0
Uses an API request for user upsert TLS terminated by AWS load balancer and passed to the application.
Client on end user desktop device (Mac or Windows)
Client application
Runs on the end user device.
Daemon service
Runs on the end user device and connected with the client application over a gRPC connection on localhost, therefore no TLS connection. If gRPC is blocked via a firewall, a fallback solution using REST is being used to establish the connection.
All External Third-Party Providers
This is an overview of all services, that are involved in managing user data outside of our environment.
- AWS
Used as the IaaS provider for running the Anchorpoint cloud metadata server. It is storing and processing all the metadata objects that are generated by the Anchorpoint desktop application. - Stripe
Used as the payment provider. It is storing and processing payment information. - Auth0
Used as the authentication providers. It stores user credentials. - Webflow
Used as a web hosting platform. It provides the user interface for certain backend services, but does not store or process user information. - MailerLite
Used for email marketing and onboarding purposes. It stores the user's email and permission to send marketing material. - Crisp
Used for customer support. It stores the user's email and the content of support discussions. - Notion
Used as the main company’s wiki tool. It stores user data. - Microsoft Office
Used as a communication tools (Microsoft teams) and document storage (Microsoft OneDrive). It stores user information. - Calendly
Used to book meetings. Stores the user's email. - Zapier
Used for business automation. It stores user data. - Linear
Used for issue tracking and bug reporting. It stores the user's email. - Sentry
Used for crash reporting.
Business processes
Change management
Each change to operational and production systems is made in the following way:
- Changes to operational and production systems are proposed by directors and employees of Anchorpoint Software GmbH.
- The executive board evaluates the proposed changes, assessing potential outcomes for the business and potential negative security impacts.
- Major changes that affect stakeholders and customers must be communicated in an appropriate time prior to implementation. The Chief Technology Officer is responsible for obtaining approvals from affected stakeholders and clients.
- Anchorpoint’s development team implements the change.
- After implementation, the change is tested in a proper staging environment. The Chief Technology Officer is responsible for ensuring that the change has been implemented according to its requirements and has not caused any negative side effects.
- The Chief Executive Officer is informed of the implementation of changes.
Incident management
Every employee, customer, and stakeholder can report an incident. Unless mandated differently, the following terms apply:
Contact in case of an incident or malfunction
- Email: support@anchorpoint.app
- Phone: +49 6434 2168144
- Microsoft Teams (for internal use): using the “General” channel
Low and medium severity
Issues of this severity are only suspicions or strange behaviors. They haven't been proven and need more looking into. There is no sign that systems are in danger and don't require immediate action. This also includes occasional crash reports by our crash reporting system.
High severity
High severity issues mean problems where somebody might take advantage or cause harm, even though it hasn't happened yet. Examples of high severity issues are vulnerabilities with a chance of being exploited, malicious programs on our systems, people accessing business information (like passwords, vulnerability data, and payment info), or any threats that might cause physical harm.
Server unavailability, which might also prevent customers from using the service are also marked as high severity.
When high severity issues are being dealt with, the subject line of the email to support@anchorpoint.app has to be marked as "Urgent" and that @general has to be mentioned in Microsoft Teams.
Critical severity
Critical issues relate to actively exploited risks and involve a malicious actor. Identification of active exploitation is critical to this severity category.
High severity issues should include a “Critical” in the subject line of the email to support@anchorpoint.app and an @general mention in Microsoft Teams. Furthermore, the CEO and CTO need to be contacted via direct message or phone.
Response times
- Low and Medium Severity: 5 hours
- High Severity: 2 hours
- Critical Severity: 1 hour
Recovery times
- Low and Medium Severity: The next scheduled software update
- High Severity: 8 hours
- Critical Severity: 4 hours
Response step
The CTO is responsible for setting up an emergency meeting with the required participants to fix technical issues, as well as informing the CEO for communicating with affected stakeholders and customers. The purpose of this meeting is to define an action plan in written form that will be executed immediately. This action plan will be stored in the company wiki and will serve for communication and retrospective purposes. Stakeholders and customers will be informed immediately via email after the incident has been properly identified and after a fix has been rolled out.
Disaster recovery
The purpose of this policy is to define the procedures for recovering Information Technology (IT) infrastructure and IT services within set deadlines in the case of a disaster or other disruptive incident. The objective of this plan is to complete the recovery of IT infrastructure and IT services within a recovery time, as described in Chapter Incident Management, based on the severity.
Incident response team
- Dennis Schlösser (CTO) | d.schloesser@anchorpoint.app
- Jochen Hunz (representation, Head of RnD) | j.hunz@anchorpoint.app
- Matthäus Niedoba (representation, CEO) | m.niedoba@anchorpoint.app
Critical services
- Anchorpoint backend server
- Kubernetes cluster with RabbitMQ message broker
- AWS RDS Instance (Relational Database Service)
Backups
Restoration of a database means that a second database (which includes the snapshot) is instantiated. A redirection will point to the new instantiated database, while the existing one is still running. More information about backups can be found in the chapter on Application Architecture.
Disaster recovery procedure
- Notify the CTO and CEO
- Identify the cause responsible for the disaster. This is normally done by the CTO during the emergency meeting
- Make sure that the cause is eliminated so that the recovery next steps can take place. If that is not the case, inform the CTO
- Prepare production system
- Turn off the Anchorpoint server. This will activate the offline mode in the Anchorpoint Desktop application
- Restore the database backup to a new AWS RDS Instance
- Test the backup on the staging system first
- Redirect the staging server to the new AWS RDS Instance
- Test the staging system using Postman to check that the data is valid
- Test the staging system using a Desktop application using the deployment test checklist
- If successful, move to the next step. If failed, redo the backup procedure
- Rollout the backup on the production system
- Redirect the production server to the new AWS RDS Instance
- Restore the S3 bucket backup
- Activate the Anchorpoint production server
- Test the production system using Postman to check that the data is valid
- Test the system using a Desktop application using the deployment test checklist
- Delete the old AWS RDS Instance
- Inform the CTO that the backup is complete
- Prepare a report based on the template
Vendor breach notification
The following steps apply to all employees, contractors, and third-party service providers with access to our systems and data. This is the standard procedure when a breach is detected in one of our third party services (AWS, Auth0 or Stripe).
- Detection and Assessment
Any suspected or confirmed data breach must be immediately reported to our Incident Response Team (IRT). The IRT is responsible for assessing the breach's impact, including which vendors are affected and the sensitivity of the compromised data. - Notification Procedure
Timing: Vendors will be notified of any breach affecting their data no later than 24 hours after the breach has been confirmed and assessed.
Method of Notification: Notifications will be sent via email from the IRT. If necessary, follow-up communications may be made via phone or encrypted messaging services.
Content: The notification will include:
- A description of what happened.
- The type of data that was affected.
- Steps we are taking to secure our systems and prevent future breaches.
- Actions the vendor should take to protect their data and systems.
- Contact information for further inquiries. - Support for Affected Vendors
We will provide support to help vendors assess the impact on their systems and mitigate potential risks. This may include offering security audits, sharing best practices for data protection, and providing timely updates as more information becomes available. - Regulatory Compliance
We will comply with all applicable laws and regulations regarding breach notification and data protection. This includes cooperating with vendors to meet their regulatory reporting obligations. - Review and Update
This policy will be reviewed annually and updated as necessary to reflect changes in legal requirements, industry standards, and our business practices.
Monitoring
Monitoring is executed using a tool called Grafana to ensure maximum availability, performance, and security of the application. The monitoring includes, but is not limited to, the following parameters:
Availability
- Availability of the application
- Accessibility of backend systems and services
Resources
- CPU utilization
- Utilization of network interfaces
- Utilization of persistent and volatile storage
Performance
- Response times of the application
- Response times of backend systems
- Query times for database contents
Security
- Update status of systems
- Error logs
- Access logs
In addition, server and site status is publicly displayed using a tool called StatusGator and is accessible via https://anchorpoint.statusgator.app/
Usage analytics
In order to improve the quality of our service and provide support, we use a telemetry system to track user events when users interact with the desktop application. This tracking includes:
- Errors
- Usage of specific features
- Account creation and deletion
- Log-in events
It does not include sensitive information such as file names or data entered by the user into fields.
Access to Services
Only authorised employees have the necessary credentials to access certain services that manage user data. Login credentials are managed by a service called Bitwarden, which also manages the associated password policies.
MFA is required to access all services that involve user data.
Employees leaving the organisation follow a pre-defined employee offboarding and access control policy, ensuring that all access is removed for unauthorised individuals.
User Data
Data at Rest
All databases use a so-called "at rest" encryption. This means that data can only be read if proper authentication takes place on the respective database system. The files in which the data is stored are stored in encrypted form so that they can only be read by database systems that have the appropriate decryption key.
Data, stored in S3 buckets are also encrypted at rest.
Data in Transit
Anchorpoint applies transport encryption whenever data has to be transmitted over an insecure or public network. The type of transport encryption depends on the encryption requested by the client system. Anchorpoint uses HTTPS connections with 256-bit SSL certificates for all communications with clients.
External Network Traffic
External network perimeters are hardened and configured to prevent unauthorized traffic. Ports and protocols are limited to those with a specific business purpose. Traffic from the public internet is only allowed to a highly available load balancer that only allows TCP traffic on ports 80 and 443. Port 80 is only allowed to forward traffic to port 443. All networks only allow the traffic that is required by our applications.
DMZ
External connections are terminated in a DMZ and the connections are recorded in event logs. The external connections are terminated at the load balancer, which is located in a DMZ-like network segment. Most traffic is immediately dropped, except for traffic on ports 9090, 80, and 443.
Inbound and Outbound Protection
Inbound and outbound points are protected by firewalls and Intrusion Detection Systems (IDS). Communications are limited to systems strictly allowed and Intrusion Prevention Systems (IPS) are used. Inbound and outbound traffic runs through the DMZ-like network segment of AWS.
DNS and IP Addresses
Ionos.com is used as a DNS provider which holds CNAME records to DNS names managed by AWS.
Data Segregation
Unless mandated otherwise, all client data within scope should be logically segregated on the service environment. If physical segregation is necessary, please contact your Anchorpoint representative.
Backups
Backups are performed daily and stored on physically separated servers (AWS S3). The backups are managed using the AWS Backup Service. Logs of the backup process are automatically created. The backup window is between 02:00-06:00 UTC.
Data Retention
User data is not deleted automatically. Data is retained indefinitely unless a deletion request is submitted by the user. Upon receiving such a request, the entire account is permanently deleted. This includes all associated workspace data, metadata, user credentials, and any related marketing or communication records.
How to create a data deletion request
To delete user data from our system, send us an email at support@anchorpoint.app with the subject “Data deletion request.” Specify the email of the account holder.
The data deletion request will be processed, and the requester will be informed accordingly.
User Account Management
Authentication
Users are forwarded to the Auth0 webpage to create an account and to authenticate before accessing the Anchorpoint desktop application. An access token is stored on the user's local computer. Auth tokens are valid for one hour and refresh tokens are valid for 30 days.
Password policies
Account creation requires a user email and a password with the following policy:
- At least 8 characters
- At least 3 of the following:
- Lower case letters (a-z)
- Upper case letter (A-Z)
- Numbers (0-9)
- Special characters (e.g. !@#$%^&*)
Single-Sign-On (SSO)
Currently, SSO is only possible with a self-hosted metadata server. It is not provided for the cloud metadata server at the moment.
For SSO, the following connection options are supported:
- Oauth2
- OIDC
- SAML
- WS-FED
In a self-hosting environment it is possible to enforce SSO for all accounts.
MFA
Multi-factor authentication is also only possible with a self-hosted metadata server. Multi-factor authentication can also be enforced for all accounts.
Rules and permissions
An Anchorpoint workspace is the place where members can be added and projects can be created. A workspace is connected to the subscription and the number of members that a customer is paying for. Members in a workspace can edit metadata and have the following roles and permissions:
Member
Members can collaborate in a workspace by editing metadata in projects to which they are assigned. They can also create new projects and invite members from the workspace to a project by knowing their name or email address. They cannot see or edit all the members of a workspace. They cannot access projects to which they are not assigned. Members can only add other members to projects when they have an explicit permission to edit the project settings.
Members can only be assigned to projects by:
- Assigning them in the project settings by admins or members who have explicit permission to change project settings
- Accessing the .approj file on the file system. Opening that file will automatically add them to the corresponding project.
Admin
Admins can do everything that members can do, but they have all the rights to modify project settings without explicit permission. They can also view all workspace members, as well as add and remove members from the workspace. Admins can also change workspace settings.
Owner
Each workspace has only one owner. An owner can do the same as an admin and change the subscription settings. An owner can purchase or remove additional seats, or cancel the subscription.
Login and authentication flow
The login flow assumes that the Anchorpoint desktop application has already been downloaded and installed correctly.
1. Initial state
The application has been opened and no user is logged in. To create an account, the user has to click on "Sign Up".

2. Account creation
When the user clicks on "Sign up", a website window opens. The sign-up form from Auth0 is opened. The user can sign up via email or use a social login via Google.

3. Opening the desktop application
After creating an account, the user is landed on a confirmation website and the desktop application is started. It receives a token from Auth0, which was created during the login process before and is able to connect to the Anchorpoint server.


Development
Software Development Lifecycle (SDLC)
The software development process follows a structured lifecycle with the following phases:
- Planning
Features and improvements are planned using GitLab issues and project boards. Prioritization is based on the RICE framework (Reach, Impact, Confidence, Effort). - Design
User interface and technical concepts are designed prior to implementation. This includes architectural planning, API structure, and UX considerations. - Development
Source code is managed using Git version control and GitLab. Code changes are submitted through merge requests and reviewed before integration to the final release. - Testing
A formal testing process is applied to all changes. This includes manual testing of new features, fixes, and improvements, as well as automated integration tests and smoke tests prior to release. - Release
- Major versions: x.0.0
Contain significant new features that affect the entire application. - Minor versions 0.x.0
Contain improvements of existing functions, as well as bugfixes, which affect only a certain part of the application and are not classified as critical. - Hotfixes 0.0.x
Contain bugfixes (non-critical as well as critical) but no major product features.
- Major versions: x.0.0
- Monitoring and Maintenance
Usage data and system performance are monitored using Matomo and Grafana. Errors and anomalies are tracked, and relevant findings are incorporated into future planning and development cycles.
Versions and Updates
Software updates are distributed approx. every month via an update system that runs in the background in the desktop application.
Critical fixes are applied based on the incident management procedure in the respective recovery time.
A changelog of features and bugfix releases can be accessed via https://www.anchorpoint.app/releases. New entries are marked with the appropriate version number.
Testing & staging
Application development takes place in a staging environment that contains no user data and runs on a separate environment from the production server.
Software Bill of Materials (SBOM)
As part of our commitment to supply chain security, Anchorpoint generates and validates a Software Bill of Materials (SBOM) for all server software. SBOM checks are performed automatically within our build pipeline for both the cloud metadata server and the self-hosted metadata server.
We use industry-standard formats such as SPDX 2.3 to describe software components, their versions, licensing information, and associated security references. An SBOM provides transparency into all third-party and open-source dependencies included in our software. This process enables proactive vulnerability management and ensures compliance with licensing obligations.
Documentation
The Anchorpoint documentation can be accessed online via docs.anchorpoint.app. It describes features of the application and is updated with each new release.